Cyber Security

Cyber security
Cyber Security Management Committee
- According to Article 38-1 of "Implementation Rules of Internal Audit and Internal Control System of Financial Holding Companies and Banking Industries", a person above Executive Vice President or with equivalent responsibilities shall be designated as CISO. In 2011, the Executive Vice President who supervised the Information Security Dept. served as the CISO to enhance the Bank's ability to implement information security issues.
- The Bank has established the "Cyber Security Management Committee" to effectively implement matters related to cyber security management. The committee is chaired by the Chief Information Security Officer, who oversees the execution and coordination of cyber security management matters. During meetings, Board member Xin-Wu Lin and Jin-Long Liu attend to Cyber Security Management Committee and provide suggestions. They also review the implementation of the Bank’s overall cyber security management. Cyber Security Management Committee also invites cybersecurity consulting experts to attend and offer professional opinions when discussing significant cybersecurity issues. They provide professional opinions on proposals regarding significant cybersecurity issues and receive consultation from the Board of Directors. The Cyber Security Management Committee convened 11 times in 2024.
- The establishment of the Cyber Security Management Committee shows the Bank's emphasis on cyber security, so that cyber security is no longer a slogan, but the implementation of the system.
Cyber Security Management Policy
- To ensure the security of the Bank’s information systems and assets, strengthen the overall cyber security framework, and reduce operational risks, the Bank has formulated the Cyber Security Management Policy. The objective of this policy is to prevent unauthorized access, use, control, disclosure, destruction, alteration, or other forms of compromise to the Bank’s systems and data, thereby safeguarding their confidentiality, integrity, and availability. In addition, the Bank continuously enhances its cyber security defense mechanisms through annual adjustments to the Information Security Maintenance Plan, implementing cybersecurity initiatives to strengthen overall cyber security.
- To ensure the security of the Bank’s cyber security systems and information assets, strengthen the overall cybersecurity framework and reduce operational risks, the Bank has formulated the Cyber Security Management Policy, and all of our employees, outsourced vendors, and visitors shall abide by our cyber security management policy to ensure the confidentiality, integrity, and availability of cyber security systems and information assets, and reduce operational risks. In addition, the Bank re-examines this Policy every year regularly or at each major change in order to ensure compliance with the latest development trends in cyber security regulations, technologies, organizations, and operations.
- To maintain the continuous operation of its information and communication (I&C) systems, the Bank has established an annual cyber security maintenance program and an incident response mechanism, and conducts regular drills to ensure business continuity. In addition, the Bank has implemented threat monitoring and response measures, as well as a cyber security incident response framework, enabling early detection and mitigation of potential risks. In the event of a cyber security incident, the Bank will follow its incident reporting procedures and major contingency handling mechanism, and, depending on the nature and severity of the incident, proactively communicate with affected stakeholders regarding the incident response and subsequent improvement measures.
- All of our employees, suppliers, and visitors shall abide by the cyber security management policy. All employees have the responsibility and obligation to protect the information assets they use. All personnel of the Bank, in the execution of tasks related to this annual cyber security maintenance program, shall be subject to rewards or disciplinary actions based on the nature and severity of their contributions or any resulting losses to the Bank, in accordance with the Bank’s "Employee Rewards and Disciplinary Guidelines" and "Employee Performance Evaluation Guidelines".
- All employees, suppliers, and visitors are required to comply with the Bank’s Cyber Security Management Policy. Employees also bear the responsibility and obligation to protect the information assets they use. While cooperating with the Bank, suppliers are required to comply with the information security and system protection requirements stipulated in the "Information Security Terms and Agreements".
- The Bank conducts an annual review of its Cyber Security Policy, or initiates a reassessment in response to significant changes, to ensure alignment with the latest developments in relevant laws, technologies, organizational structures, and operational practices. To validate the effectiveness of the Bank’s overall information security implementation, a third-party organization is engaged each year to perform an independent assessment. Based on the results, the Bank consolidates key information including the execution status of security protection mechanisms, reporting of cybersecurity incidents, and feedback from internal and external stakeholders. A comprehensive report on the Bank’s information security implementation for the preceding year is submitted to the Board of Directors in the first quarter of each year.

Risk management framework
- To ensure the effective implementation of information and communication security operations, the Bank adopts the Three Lines of Defense model to define clear responsibilities and maintain a robust security framework. The first line of defense comprises the Bank’s I&C system management and user departments, responsible for the design and execution of security controls. The second line of defense is the Information Security Department, which is responsible for the planning and oversight of I&C security management operations. The third line of defense is the Board of Directors’ Audit Office, which performs independent audits to evaluate the effectiveness of I&C security operations, including access control, protective measures, and security incident reporting.
- In order to ensure that the operation process has been adjusted to the most appropriate state, dedicated person will be assigned to take on-the-spot counseling from time to time to assist relevant units to improve cyber security operations as soon as possible.
- Submit the bank's cyber security handling situation to the risk management committee every month, and submit the information security handling situation to the Cyber Security Management Committee for review every quarter, and then submit it to the board of directors for report, so as to improve the board of directors' understanding of the bank's cyber security status.
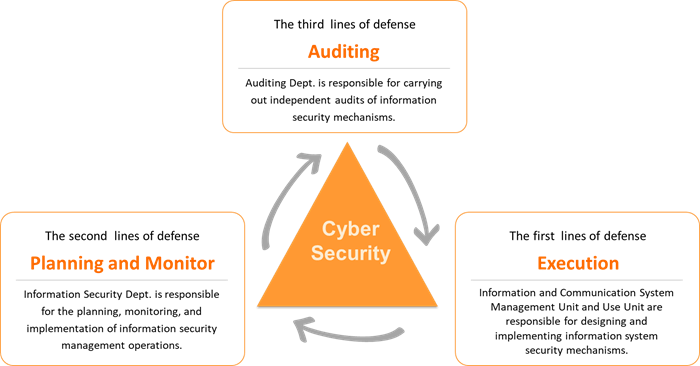
The Bank’s cyber security risk management framework is based on the “Three Lines of Defense.” The first line consists of all system management and user departments, responsible for the design and execution of controls. The second line is the Information Security Department, responsible for planning and overseeing cyber security management operations. The third line is the Audit Department under the Board of Directors, which performs independent audits to evaluate the effectiveness of cyber security operations, including access control, security protection, and incident reporting.
Introduce international cyber security management standards and obtain certification: To ensure the confidentiality, integrity, and availability of customer data and related operational information, the Bank obtained "ISO 27001 Information Security Management System" international standard certification in November 2010 and has maintained the validity of the certificate every year (the certificate is valid until November 6, 2025).
Notification process for cyber security incidents
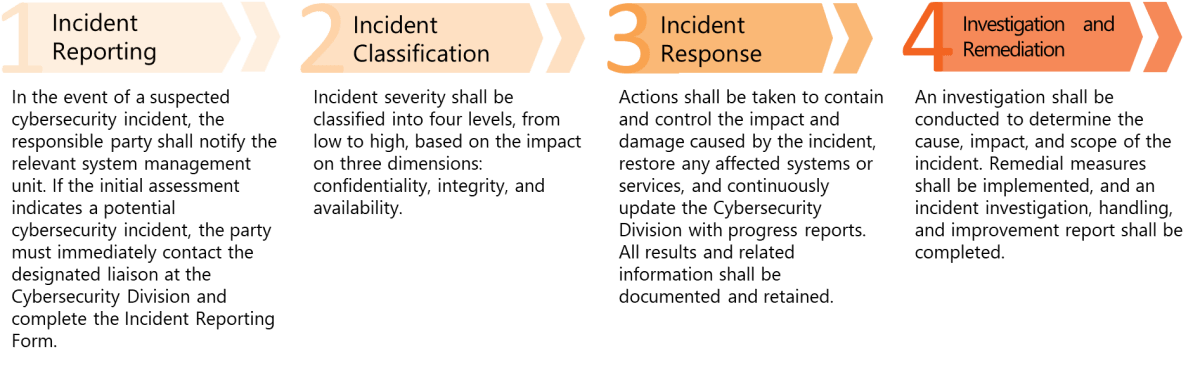
The Bank has established a clear reporting mechanism requiring employees, upon discovering or becoming aware of a potential or actual cyber security incident, to follow the Bank’s incident reporting procedures. They must promptly carry out damage control, recovery, investigation, and remediation. Cyber security incidents are classified and handled based on their severity, and, when necessary, escalated to senior management or competent authorities. All incidents are fully documented and monitored throughout the process to ensure timely risk management and effective response.
Concrete management programs, and investments in resources for cyber security management
- Implement the cyber security mechanism: Implement "Diversity and Defense-in-Depth", including network control, webpage control, email control, and endpoint control systems, in order to enhance cyber security defense capability. Use the "Cybersecurity Assessment Tool" (CAT) to conduct cyber security governance maturity assessments, continuously enhancing the Bank's cyber security.
- Perform cyber security protection checks: In order to ensure the security of the information communication system, the Bank regularly performs cyber security protection checks operations. In 2024, it has implemented a computer system information security assessment project, a Distributed Denial of Service (DDoS) drill, and the bank’s personal computers and business workstation weaknesses Scan and detect operations to confirm the completeness and effectiveness of existing control measures. In addition, red team vs blue team attack-defense drills are conducted through professional organizations to strengthen defense detection and response capabilities in response to attacks.
- Expand cyber security intelligence and cooperation: The Bank has joined collaborative cyber security organizations for financial institutions, such as the Financial Information Sharing and Analysis Center (F-ISAC), and has designated dedicated personnel to receive and process cyber threat intelligence. Based on the recommendations and assessments received, the Bank updates system configurations and settings as needed, and tracks remediation progress to ensure timely and effective response to emerging threats. These measures help the Bank stay abreast of evolving cyber threat landscapes and formulate appropriate control and mitigation strategies. The Bank has established a Security Operations Center (SOC) and deployed professional cyber security monitoring personnel to monitor threats such as internal abnormal behaviors and external attacks through a Security Information and Event Management (SIEM) platform to ensure the effectiveness of cyber security protection monitoring.
- Strengthen employees’ awareness of information security: In the 2024 years, the Bank has completed a 3-hour information security awareness course for all staff and a 15-hour professional courses of information security or on-the-job training for information security staff to enhance information security awareness and capabilities. Provide information security education and training for directors, supervisors and senior management personnel, enhance Board of Directors members’ understanding of the cyber security situation. In order to strengthen colleagues' alertness to social emails, a total of 8 email social engineering drills were conducted in 2024.
- Establish a business continuity mechanism: The Bank has established the annual cyber security maintenance program and cyber security incident response mechanism, and holds regular drills to reduce any impact caused by a disaster or major event on business continuity. In 2024, it has finished Information Communication System Business Continuing Planning exercises. Since 2024, the Bank has been insured with "Electronic and Computer Crime Comprehensive Insurance" to transfer financial losses caused by external malicious actors or hackers infiltrating the systems.
- Cyber security incident management: To enhance its response capabilities to cyber security incidents, the Bank has established the Regulations on the Notification and Response of Cyber Security Incidents and set up a "Computer Security Incident Response Team"(CSIRT), with the Bank's Chief Information Security Officer serving as the convener, to promptly handle cyber security incidents and mitigate damages.
- The funding invested in cyber security in 2024 accounted for 23.92% of the total IT budget.


